Introduction
In the realm of GDPR compliance, Pseudonymisation emerges as a critical tool, delicately substituting identifiable markers with artificial identifiers. Unlike anonymization, which strips data of identifiers irreversibly, pseudonymisation retains data as personal under GDPR while ensuring a level of anonymity.
Article 4(5) of the GDPR defines pseudonymisation as a dynamic process, crucial for unlinking personal data without the need for separate, securely stored information. This adaptability is its key strength in an ever-evolving data landscape. The CoC emphasizes that pseudonymised data remains personal data under GDPR unless re-identification is impossible.
While incorporating encryption among its techniques, pseudonymisation extends beyond encryption alone, encompassing hashing, masking, and more, ensuring a multi-layered approach to data security.
This platform is dedicated to establishing a new Code of Conduct (CoC) for pseudonymisation, aiming to make it accessible to companies seeking compliance while offering policymakers and data protection authorities essential insights. Delve into transformation techniques, access controls, transparency, and data subject rights— shaping the future landscape of data transfers under the GDPR.
Identification of the Data Subject:
The GDPR defines identifiable information broadly. Pseudonymisation reduces this identification risk by replacing or removing certain identifiers with pseudonyms. However, if re-identification is possible with accessible additional information, pseudonymised data is considered personal unless proven impossible to re-identify.
Compatibility Test, Article 6(4) GDPR:
The GDPR allows additional data processing if it aligns with the initial purpose. Pseudonymisation can serve as a safeguard for compatibility, but it doesn't automatically guarantee compatibility. Each case must undergo a contextual assessment considering factors like the data's nature, consequences for subjects, and existing safeguards.
Privacy by Design/Default:
Data controllers must embed privacy measures into their systems. Pseudonymisation aids in data minimization and ensures that only necessary personal data are processed by default, aligning with GDPR principles of privacy by design and default.
Data Breach, Articles 33/34 GDPR:
Pseudonymisation can limit the impact of data breaches by making it challenging for attackers to link data to individuals. This impacts the obligations of controllers and processors under Articles 33/34 of the GDPR, potentially exempting or delaying notification if pseudonymisation ensures data cannot be attributed without separate secure information.
Requirements of Pseudonymisation
Transformation Processes (Techniques):
Various techniques (encryption, hashing, tokenisation, masking, etc.) can pseudonymise data based on factors like data type, sensitivity, processing context, recipients, and retention policies. The chosen technique should effectively de-identify data while preserving utility for intended purposes.
Technical and Organisational Measures:
To prevent re-identification, related information must be kept separately and protected by appropriate technical and organisation measures, such as encryption, restricted access, storage separation, audits, policies, staff training, and third-party agreements.
Access Controls:
Only authorized personnel should access and process pseudonymised data and additional information using mechanisms like authentication, authorization, accountability, and least privilege principle. Regular reviews are essential, especially during staff or role changes.
Transparency:
Data controllers must ensure transparency in pseudonymisation, particularly regarding processing contexts and safeguards. The Code requires clear documentation of pseudonymisation processes and data transfers, including international transfers. If pseudonymised data is transferred outside the EEA, data subjects must be informed.
Rights of Data Subjects:
Data subjects retain their GDPR rights over pseudonymised data unless fulfilling them is technically impossible or disproportionately difficult. The Code reinforces GDPR principles, emphasizing safeguards against unauthorized re-identification and ensuring that data is processed only as long as necessary.
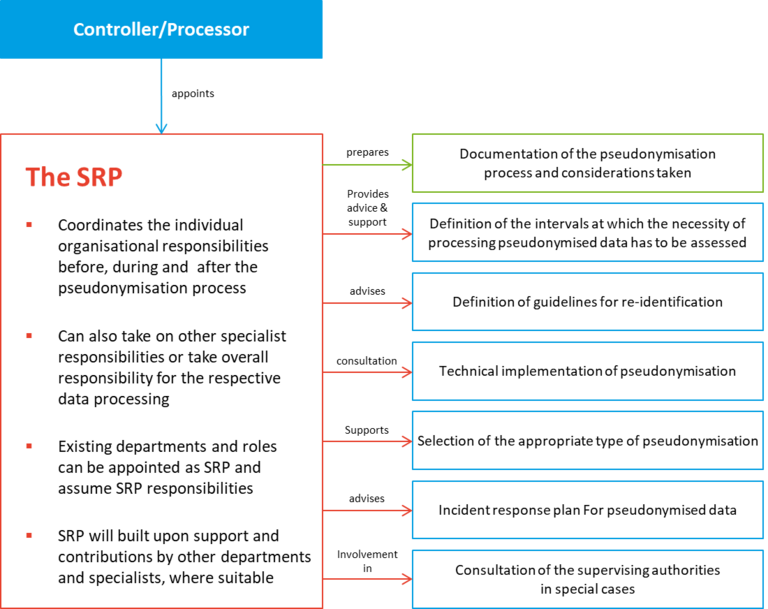
Setup for Pseudonymisation by SRP
Intention
Pseudonimisation can be implemented by several means (see above). The individual methods and required technical and organizational measures must be determined with adequate expertise and rigor.
The Code of Conduct requires the establishment of distinct procedures and points of contact with suitable expertise, allowing for adequate practical yet data protection friendly implementation.
As a guidance, the Code provides for annexes outlining examples of how pseudonisation might be implemented for distinct processing contexts, alongside explanations how such implementation was determined following the logics and requirements of the Code.
General Assembly
The General Assembly comprises the esteemed "founding members" of the CoC, serving as the cornerstone of this collective initiative. Additionally, signing entities seeking GA membership contribute to this esteemed body. The GA shoulders critical responsibilities within the CoC framework, including the approval of fees, admission or revocation of GA membership, and endorsing alterations to the Code. Moreover, it holds the authority to sanction changes proposed by the Steering Board, ensuring collective governance and alignment with CoC objectives.
Steering Board
The Steering Board (SB) holds a central role as the guiding force behind the CoC, comprising influential entities such as Bitkom and GDD, assuming chair positions for two-year terms. It encompasses representatives pending SB approval, from both private and public sectors, invited based on expertise, along with esteemed data protection and pseudonymisation experts.
Within its purview, the SB undertakes critical tasks pivotal to the CoC's functionality and evolution. It actively proposes changes to the Code and recommends adjustments concerning the fee model. Additionally, the SB diligently monitors legal and regulatory developments concerning pseudonymisation and actively participates in refining the Code monitoring mechanisms in collaboration with the monitoring body. Moreover, it assumes a vital role in the appointment and restructuring of monitoring bodies, ensuring effective oversight and governance within the CoC framework.
Monitoring Process: Ensuring Consistency and Accessibility
The monitoring process within the CoC stands as a recurrent assessment of each service, ensuring compliance with set standards. Evaluations are based on a random sample (single sampling), although in cases where compliance isn't met, a backup system of double sampling is considered.
Consistency remains a cornerstone; thus, the approach towards the Code and Monitoring is meticulously aligned. This is crucial, as monitoring must be in harmony with associated risks for data subjects while ensuring accessible pricing does not compromise effective oversight.
Standardization plays a key role, with assessments primarily reliant on standardized questionnaires. To streamline processes, maintaining detailed responses for immediate availability is a requirement. Pricing strategies aim for accessibility, particularly for small and medium-sized enterprises (SMEs). Aiming for equitable pricing, the intention is to maintain similar pricing structures for medium-sized enterprises as for small ones, albeit with possible slight adjustments to sustain economic accessibility for smaller entities. Factors influencing pricing encompass annual turnover, among other considerations, in the quest for economically feasible pricing across the board, including non-SME entities.
Governance CoC Stakeholders
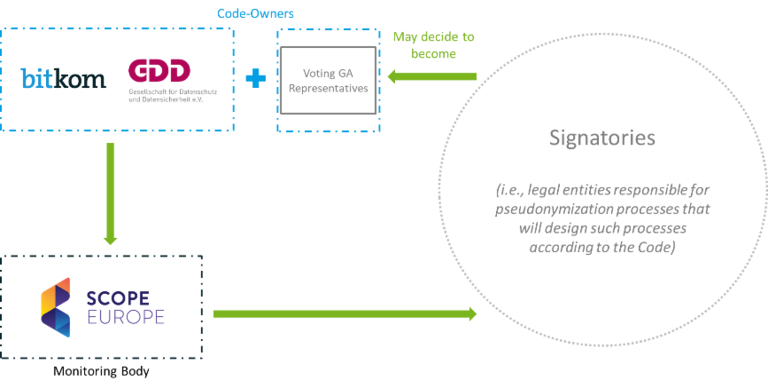
Code Supporter = Licensee of CoC parts
General Assembly = General Assembly of all signing entities
Signing Entities = Organisations complying with the CoC
Monitoring Body = Selbstregulierung Informationswirtschaft e.V. / SCOPE Europe
Steering Board = Expert panel advising the Code Owners /GA
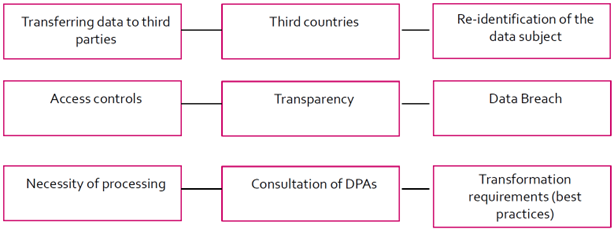
Documentation (Accountability)

Mandatory checkpoints for pseudonymization
Contributors
The draft was developed with contributions of numerous stakeholders. Those were, additionall to Bitkom, GDD und SRIW / SCOPE Europe
- Axciom Deutschland GmbH
- Bundesdruckerei GmbH
- Deutsche Telekom AG
- Media Broadcast GmbH
- United Internet AG
- Stiftung Datenschutz
Further Information and News
Further Information on Pseudonomisation is available in our reports.
SRIW comments on EDPB’s Guidelines 01/2025 (Pseudonymization)
SRIW welcomes the EDPB Guidelines 01/2025 on Pseudonymisation as an important step toward reinforcing pseudonymisation as a key safeguard under the…
Bitkom und GDD vereinheitlichen Pseudonymisierung in der Datenverarbeitung
Der Digitalverband Bitkom und die Gesellschaft für Datenschutz und Datensicherheit wollen EU-weite Verhaltensregeln für Pseudonymisierungen in der…